Firewall feature inside Artica
Artica Firewall feature protects PCs, servers or any other connected devices from hostile intrusions from the Internet and/or external networks.
It enables stateful packet filtering, Network Address Translation (NAT) and Port Address Translation (PAT) and is fully customizable to fit your needs.
There is no need for any UNIX skills, no need to use the command line for anything, and no need to ever manually edit any rule sets.
Users familiar with commercial firewalls catch on to the web interface quickly, though there can be a learning curve for users not familiar with commercial-grade firewalls
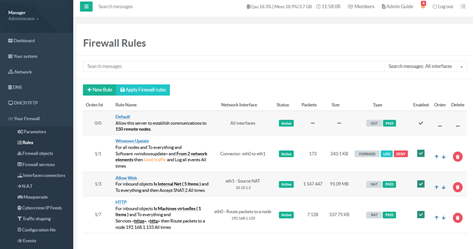
Iptables(netfilter) based firewall
Artica Firewall feature is an iptables(netfilter) based firewall system designed around the essential needs of today’s Internet deployed servers and the unique needs of custom deployed Artica installations.
The Web administration console is designed to be very informative and present the user with an easy to follow process
- Real-time logging web console.
- Cybercrime IP Feeds is a feature that downloads regularly compromised IP addresses found in the Internet. It prevents your server to be attacked by already ban a bulk of IP addresses.
- Geo-Location module allows you to define rules against location of Public IP addresses.
- Deep Packet inspection module allows you to create rule against more than 239 detected applications in both HTTP/HTTPs protocols.
- Traffic shapping module is An high-performance implementation of committed access rate, or simply rate limiting, or policing.
- Time restriction module restricting Access By Time Of The Day.It allows you to control access based upon day and time.
